
HOME < Technology < About ZeroTier
What is the ZeroTier
ZeroTier is a decentralized network virtualization platform and built atop a cryptographically secure global peer to peer network. It provides advanced network virtualization and management capabilities on par with an enterprise SDN switch, but across both local and wide area networks and connecting almost any kind of app or device. It allows all networked devices, VMs, containers, and applications to communicate as if they all reside in the same physical data center or cloud region. It has two conceptually separate but closely coupled layers in the OSI model sense: VL1 and VL2. VL1 is the underlying peer to peer transport layer, the “virtual wire”, while VL2 is an emulated Ethernet layer that provides operating systems and apps with a familiar communication medium.
ZeroTier Terminology
ZeroTier network is based on UDP protocol, which mainly consists of three parts for Planet server, Moon server, and client node LEFA.
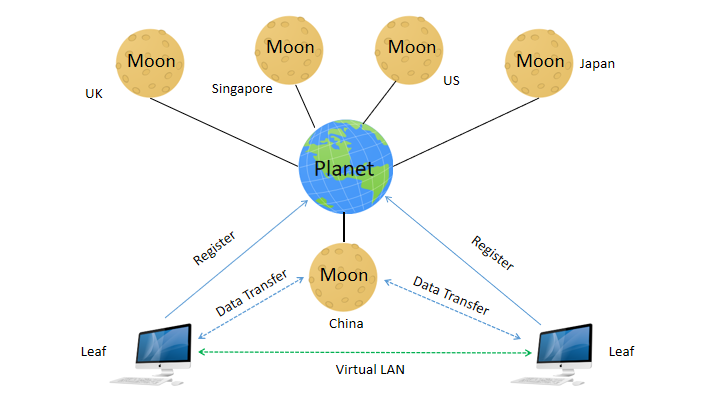
The planet server is the root node of ZeroTier, and can be built using the official server of ZeroTier or open-source code. It's used to manage address information of all ZeroTier clients and help establish direct links during clients, and serve as relay servers to forward traffic during devices when the direct links cannot be established.
The moon server is between the planets and the client, and the official planets are all located abroad. Therefore, a moon server can be built on the nearby public network, and the client can prioritize using moon nodes with lower latency for P2P connectivity or network transfer.
The client node (LEAF) can be installed on the client for remote network access, or it can be deployed to enable the route forwarding function. After configuring Static routing, two networks can be networked.
ZeroTier Network Infrastructure
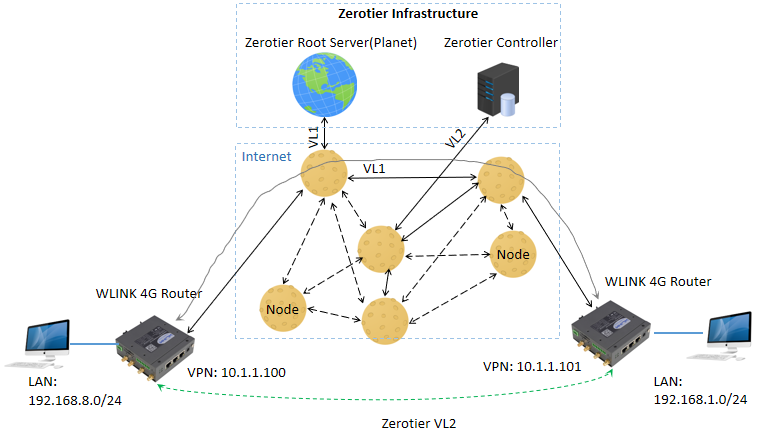
VL1
A global data center requires a global wire closet.
In conventional networks L1 (OSI layer 1) refers to the actual CAT5/CAT6 cables or wireless radio channels over which data is carried and the physical transceiver chips that modulate and demodulate it. VL1 is a peer-to-peer network that does the same thing by using encryption, authentication, and a lot of networking tricks to create virtual wires on a dynamic as-needed basis.
VL2
VL2 is a VXLAN-like network virtualization protocol with SDN management features. It implements secure VLAN boundaries, multicast, rules, capability-based security, and certificate-based access control.
VL2 is built atop and carried by VL1, and in so doing it inherits VL1's encryption and endpoint authentication and can use VL1 asymmetric keys to sign and verify credentials. It's important to understand that there is no relationship between VL2 virtual networks and VL1 paths.
Network Identifier
Each VL2 network (VLAN) is identified by a 64-bit (16 hex digit) ZeroTier network ID that contains the 40-bit ZeroTier address of the network's controller and a 24-bit number identifying the network on the controller.
Controller
Every ZeroTier virtual network has a network controller responsible for admitting members to the network, issuing certificates, and issuing default configuration information. The controller distributes the network configuration among the clients. It also uses cryptographic methods to authenticate devices. It’s the configuration manager of virtual networks (VL2). A single controller can in handle up to 2^24 networks and even more devices. If running your own controllers, you can deploy multiple instances to handle even more networks.
Network controllers are configuration managers and certificate authorities that belong to VL2.
When a node joins a network or requests a network configuration update, it sends a network config query message (via VL1) to the network's controller. The controller can then use the node's VL1 address to look it up on the network and send it the appropriate certificates, credentials, and configuration information.
ZeroTier Addressing
Every node is uniquely identified on VL1 by a 40-bit (10 hex digit) ZeroTier address. This address is computed from the public portion of a public/private key pair. A node's address, public key, and private key together form its identity. On devices running ZeroTier One the node identity is stored in identity.public and identity.secret in the service's home directory.
When ZeroTier starts for the first time it generates a new identity. It then attempts to advertise it upstream to the network. In the very unlikely event that the identity's 40-bit unique address is taken, it discards it and generates another. ZeroTier addresses are, once advertised and claimed, a very secure method of unique identification.
When a node attempts to send a message to another node whose identity is not cached, it sends a whois query upstream to a root. Roots provide an authoritative identity cache.
ZeroTier Security
Packets are end-to-end encrypted and can't be read by unauthorized parties. Every peer on VL1 possesses a globally unique 40-bit ZeroTier address, but, unlike IP addresses, these are opaque cryptographic identifiers that encode no routing information. Packets are end-to-end encrypted and can't be read by roots or anyone else, It's used modern 256-bit crypto as asymmetric public key encryption is Curve25519/Ed25519, a 256-bit elliptic curve variant.
Every VL1 packet is encrypted end to end using (as of the current version) 256-bit Salsa20 and authenticated using the Poly1305 message authentication (MAC) algorithm. MAC is computed after encryption (encrypt-then-MAC) and the cipher/MAC composition used is identical to the NaCl reference implementation.
ZeroTier Advantages
Low latency
ZeroTier offers very low latency connections compared to traditional VPNs, once a peer-to-peer connection has been established. Existing bandwidth is used efficiently and users rarely face latency issues.
Easy to deploy
Easy to set up ZeroTier in minutes with remote, automated deployment.
Flexibility
Emulates Layer 2 Ethernet with multipath, multicast, and bridging capabilities, Auto NAT Traversal.
Security
ZeroTier's zero-trust networking solution provides scalable security with 256-bit end-to-end encryption.
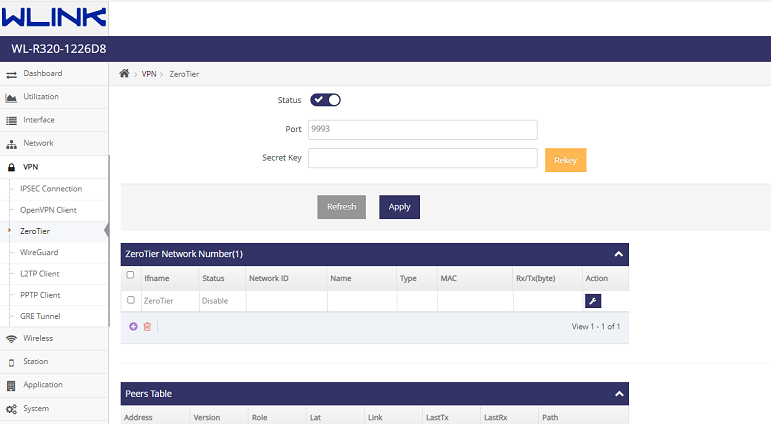
ZeroTier In WLINK Router
-- The end











