
HOME < Technology < How to configure L2TP
What is L2TP?
L2TP (layer 2 Tunneling Protocol) as originally defined in RFC 2661, establishes a point-to-point L2TP tunnel on a public network (such as the Internet), and PPP (point-to-point Protocol) data frames are encapsulated and transmitted through L2TP tunnel, which can help remote users (such as enterprises' overseas offices and business travelers) to access to enterprises through L2TP tunnel, and access to the internal network of enterprises. So, it will provide a safe, economic and effective way for remote access of private network.
L2TP Typical Network
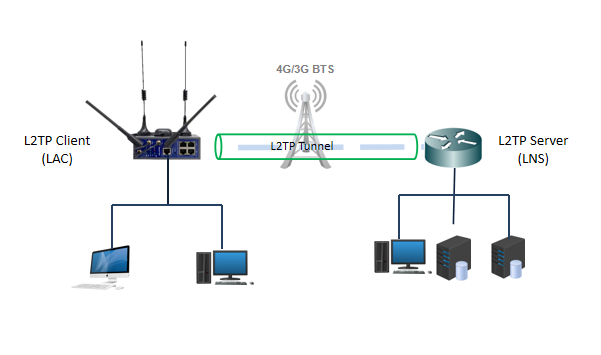
(1) LAC
LAC (L2TP access concentrator) is a device attached to the switching network. The LAC has a PPP terminal system and delivers L2TP processing. It usually provides access services for PPP users. The LAC is located between the L2TP network server (LNS) and a user, used to transfer information packets between the LNS and the user. The LAC encapsulates the information packets received from the user based on L2TP and delivers the information packets to the LNS. In addition, it decapsulates information packets received from the LNS and delivers the information packets to the user.
(2) LNS
LNS (L2TP network server) is not only the logical endpoint of PPP system, but also the L2TP server. Generally speaking, it is an edge of intranet.
As one side of an L2TP tunnel endpoint, the LNS is a peer to the LAC. The LNS is the logical termination point of a PPP session that is being tunneled from the remote system by the LAC. By establishing an L2TP tunnel on the public network, the peer end of a PPP session is logically extended from the LAC to the LNS on the enterprise intranet.
L2TP Packet Structure
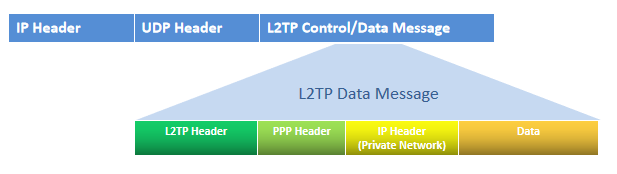
L2TP Heard Structure as below.
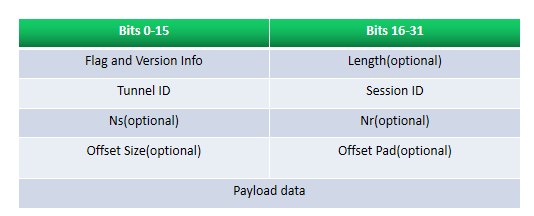
Flags and Version info Control flags indicating data/control packet and presence of length, sequence, and offset fields.
Length (optional) Total length of the message in bytes, present only when length flag is set.
Tunnel ID Indicates the identifier for the control connection.
Session ID Indicates the identifier for a session within a tunnel.
Ns (optional) sequence number for this data or control message, beginning at zero and incrementing by one (modulo 216) for each message sent. Present only when sequence flag set.
Nr (optional) sequence number for expected message to be received. Nr is set to the Ns of the last in-order message received plus one (modulo 216). In data messages, Nr is reserved and, if present (as indicated by the S bit), MUST be ignored upon receipt.
Offset Size (optional) Specifies where payload data is located past the L2TP header. If the offset field is present, the L2TP header ends after the last byte of the offset padding. This field exists if the offset flag is set.
Offset Pad (optional) Variable length, as specified by the offset size. Contents of this field are undefined.
Payload data Variable length (Max payload size = Max size of UDP packet − size of L2TP header)
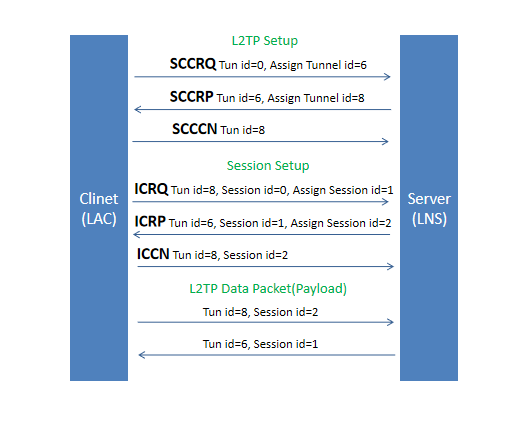
How L2TP Works
L2TP is a connection-based protocol. The process of establishing tunnel to deliver PPP session includes two steps.
(1) Establish a tunnel control connection.
(2) According to the request of the incoming/outgoing call, trigger to establish a session.
At the time of setup of L2TP connection, many control packets are exchanged between the server and the client to establish tunnel and session for each direction. One peer requests the other peer to assign a specific tunnel and session id through these control packets. Then using this tunnel and session id, data packets are exchanged with the compressed PPP frames as payload.
The list of L2TP messages handshaking between LAC and LNS as following.
L2TP Advantages
(1) L2TP can be paired up with IPSec to offer a decent level of online security.
(2) L2TP is readily available on many Windows and MAC OS platforms since it’s built into them. It also works on many other devices and operating systems.
(3) L2TP is fairly easy to set up, and that goes the same for L2TP/IPSec.
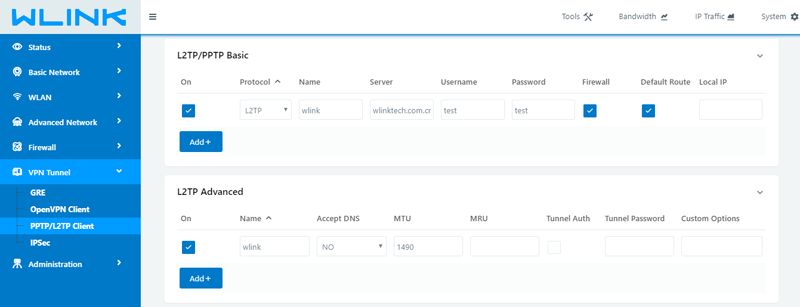
L2TP In Wlink 4G Router
-- THE END











