
HOME < Technology < IPsec
1. Overview
Internet Protocol Security (IPsec) is a secure network protocol suite that authenticates and encrypts the packets of data to provide secure encrypted communication between peers over an Internet Protocol network. IPsec uses cryptographic security services to protect communications over Internet Protocol (IP) networks. It supports network-level peer authentication, data-origin authentication, data integrity, data confidentiality (encryption), and replay protection.
As an open standard as a part of the IP suite, IPsec uses the following protocols to perform various functions.
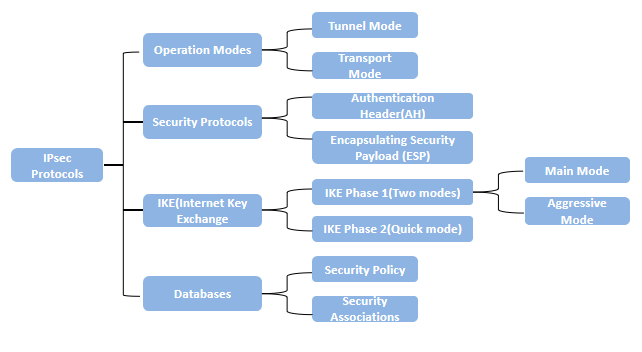
2. IPsec Basic Concepts
2.1 Security Associations (SA)
Security Associations (SA) provides the bundle of algorithms and data that provide the parameters necessary for AH and/or ESP operations. The Internet Security Association and Key Management Protocol (ISAKMP) provides a framework for authentication and key exchange, with actual authenticated keying material provided either by manual configuration with pre-shared keys, Internet Key Exchange (IKE and IKEv2), Internet Negotiation of Keys (KINK), or IPSECKEY DNS records.
2.2 Internet Key Exchange Protocol (IKE)
Internet Key Exchange (IKE) is the protocol used to set up a secure, authenticated communications channel between two parties. IKE typically uses X.509 PKI certificates for authentication and the Diffie–Hellman key exchange protocol to set up a shared session secret.
The IKE protocol uses UDP packets, usually on port 500, and generally requires 4–6 packets with 2–3 round trips to create an SA (security association) on both sides. The negotiated key material is then given to the IPsec stack. For instance, this could be an AES key, information identifying the IP endpoints and ports that are to be protected, as well as what type of IPsec tunnel has been created. The IPsec stack, in turn, intercepts the relevant IP packets if and where appropriate and performs encryption/decryption as required.
2.3 Encryption and Authentication Algorithms
IPsec is a collection of cryptography-based services and security protocols that protect communication between devices that send traffic through an untrusted network.
2.3.1 Encryption Algorithms
Encryption algorithms protect the data so it cannot be read by a third-party while in transit. Below are three main encryption algorithms.
1) DES (Data Encryption Standard) — Uses an encryption key that is 56 bits long. This is the weakest of the three algorithms.
2) 3DES (Triple-DES) — An encryption algorithm based on DES that uses DES to encrypt the data three times.
3) AES (Advanced Encryption Standard) — The strongest encryption algorithm available. AES encryption keys of lengths for 128, 192, or 256 bits.
2.3.2 Authentication Algorithms
Authentication algorithms verify the data integrity and authenticity of a message. Below are three main authentication algorithms.
1) HMAC-MD5 (Hash Message Authentication Code — Message Digest Algorithm 5) MD5 produces a 128-bit (16 byte) message digest, which makes it faster than SHA1 or SHA2.
2) HMAC-SHA1 (Hash Message Authentication Code — Secure Hash Algorithm 1) SHA1 produces a 160-bit (20 byte) message digest. Although slower than MD5, this larger digest size makes it stronger against brute force attacks.
3) HMAC-SHA2 (Hash Message Authentication Code — Secure Hash Algorithm 2)
There are three variants of SHA2 with different message digest lengths.
SHA2-256 — produces a 265-bit (32 byte) message digest
SHA2-384 — produces a 384-bit (48 byte) message digest
SHA2-512 — produces a 512-bit (64 byte) message digest
SHA2 is stronger than either SHA1 or MD5.
2.4 IPsec Security Protocols
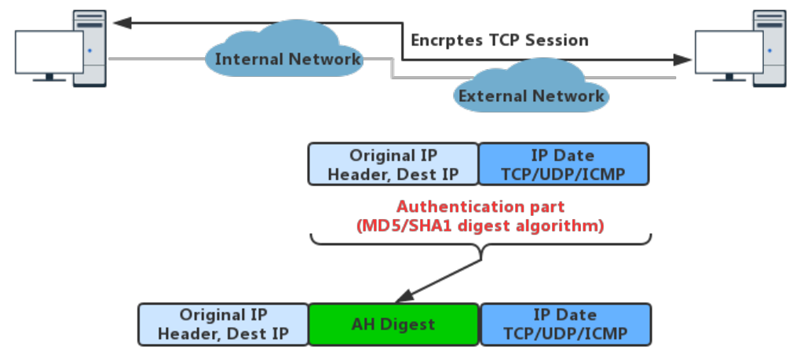
2.4.1 Authentication Headers (AH)
AH protocol provides a mechanism for authentication only. AH provides data integrity, data origin authentication, and an optional replay protection service. Data integrity is ensured by using a message digest that is generated by an algorithm such as HMAC-MD5 or HMAC-SHA. Data origin authentication is ensured by using a shared secret key to create the message digest. Replay protection is provided by using a sequence number field with the AH header. AH authenticates IP headers and their payloads, with the exception of certain header fields that can be legitimately changed in transit, such as the Time To Live (TTL) field.
Authentication Headers (AH) provides connectionless data integrity and data origin authentication for IP datagrams and provides protection against replay attacks.
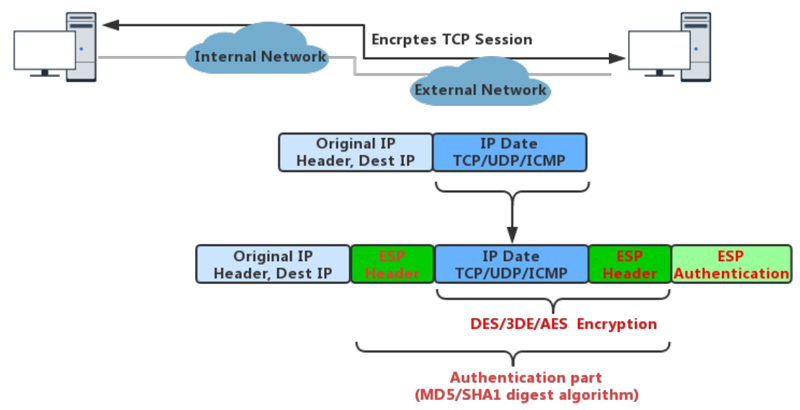
2.4.2 Encapsulating Security Payloads (ESP)
ESP protocol provides data confidentiality (encryption) and authentication (data integrity, data origin authentication, and replay protection). ESP can be used with confidentiality only, authentication only, or both confidentiality and authentication. When ESP provides authentication functions, it uses the same algorithms as AH, but the coverage is different. AH-style authentication authenticates the entire IP packet, including the outer IP header, while the ESP authentication mechanism authenticates only the IP datagram portion of the IP packet.
2.5 IPsec Operation Modes
2.5.1 Tunnel Mode
In tunnel mode, the entire IP packet is encrypted and authenticated. It is then encapsulated into a new IP packet with a new IP header. Tunnel mode is used to create virtual private networks for network-to-network communications (e.g. between routers to link sites), host-to-network communications and host-to-host communications. Tunnel mode supports NAT traversal.
2.5.2 Transport Mode
In transport mode, only the payload of the IP packet is usually encrypted or authenticated. The routing is intact, since the IP header is neither modified nor encrypted; however, when the authentication header is used, the IP addresses cannot be modified by network address translation, as this always invalidates the hash value. The transport and application layers are always secured by a hash, so they cannot be modified in any way, for example by translating the port numbers. NAT traversal is not supported with the transport mode.
MSS is higher, when compared to Tunnel mode, as no additional headers are required.
The transport mode is usually used when another tunneling protocol (such as GRE, L2TP) is used to first encapsulate the IP data packet, then IPsec is used to protect the GRE/L2TP tunnel packets.
3. How IPsec works
There are two phases to build an IPsec tunnel as IKE phase 1 and IKE phase 2.
3.1 IKE Phase 1
In IKE phase 1, first the IPsec peers are authenticated thus protecting the identities of the peers. Then the Internet Key Exchange (IKE) Security Associations (SA) policy is negotiated among the peers. This results in both the parties to have a shared secret matching key that helps in the IKE phase two. Also, in this phase, there is setting up of a secure tunnel through which the exchange of information for phase two will occur.
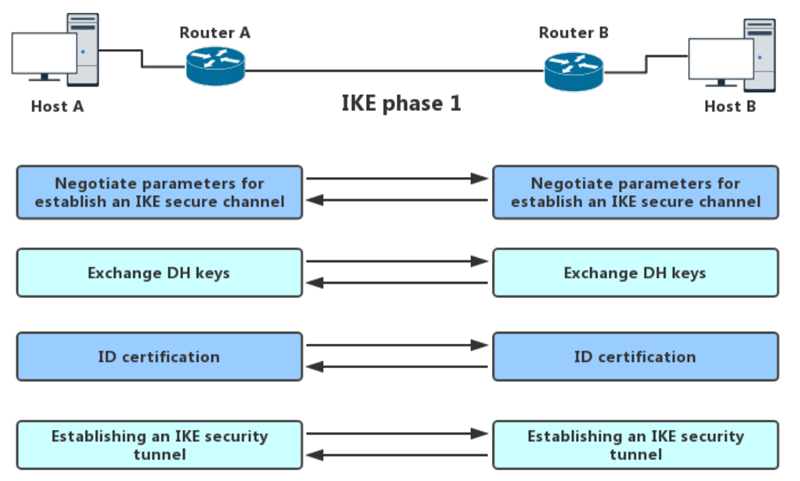
This phase has two operating modes.
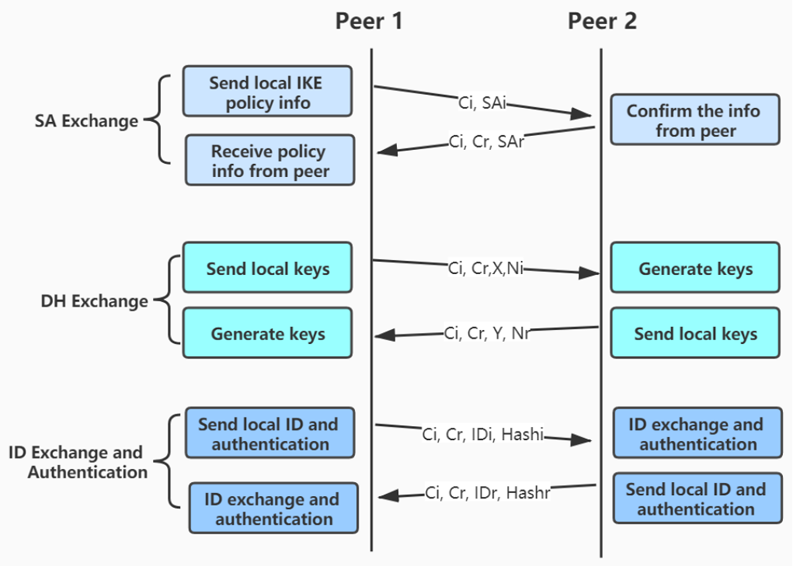
1)Main Mode
There are three exchanges among the initiator and the receiver. In first exchange, algorithms and hashes are exchanged. The second exchange is responsible for generations of shared secret keying using Diffie-Hellman exchange. The last exchange is for the verification of the other side’s identity. All three of these exchanges are bi-directional.
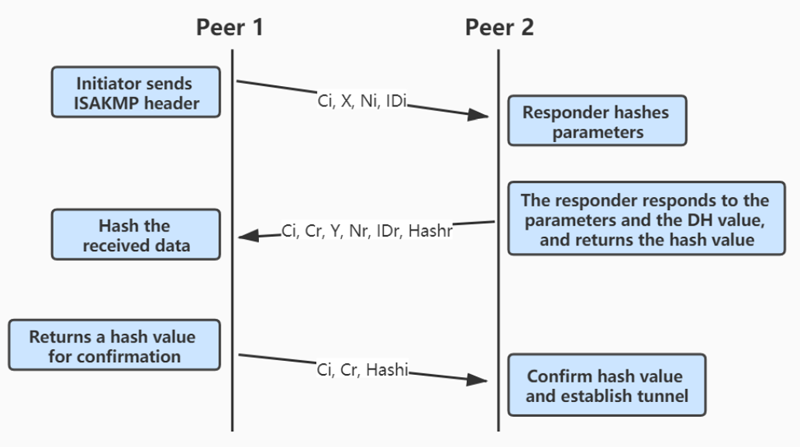
2)Aggressive Mode
There are fewer exchanges in this mode. All the required information is squeezed making it faster to use. The only trouble is that information is shared before there is a secure channel making this mode vulnerable.
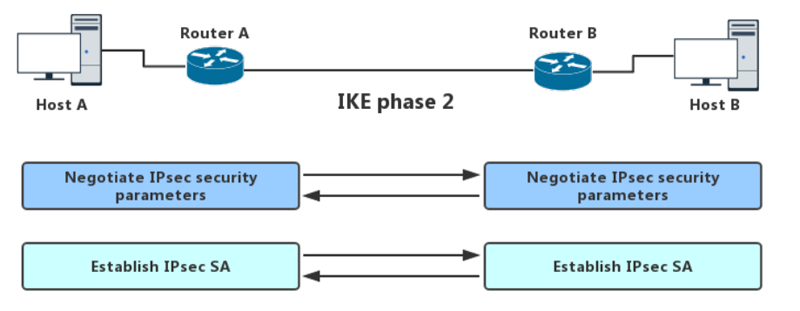
3.2 IKE Phase 2
This phase negotiates information for IPsec SA parameters through the IKE SA. Here as well IPsec policies are shared and then establish IPsec SAs. There is only a single mode (quick mode) in this phase. It exchanges nonce providing replay protection. These nonces generate new shared secret key material. If the lifetime for IPsec expires, it can renegotiate a new SA.
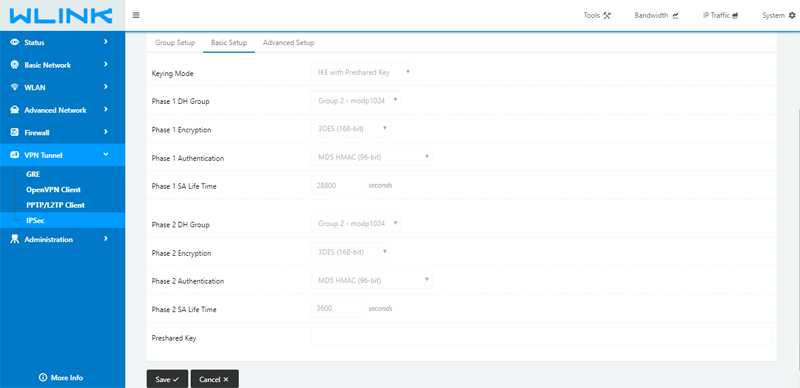
4. IPSec In Wlink 5G/4G Router
-- The End











